Unpatched Vulnerabilities Continue to be a Major Issue – How Can We Fix Them?
April 13, 2021
We can all agree there is room for improvement in patching your systems.
Let me make the case. On March 11th Microsoft acknowledged the existence of a vulnerability within Exchange.
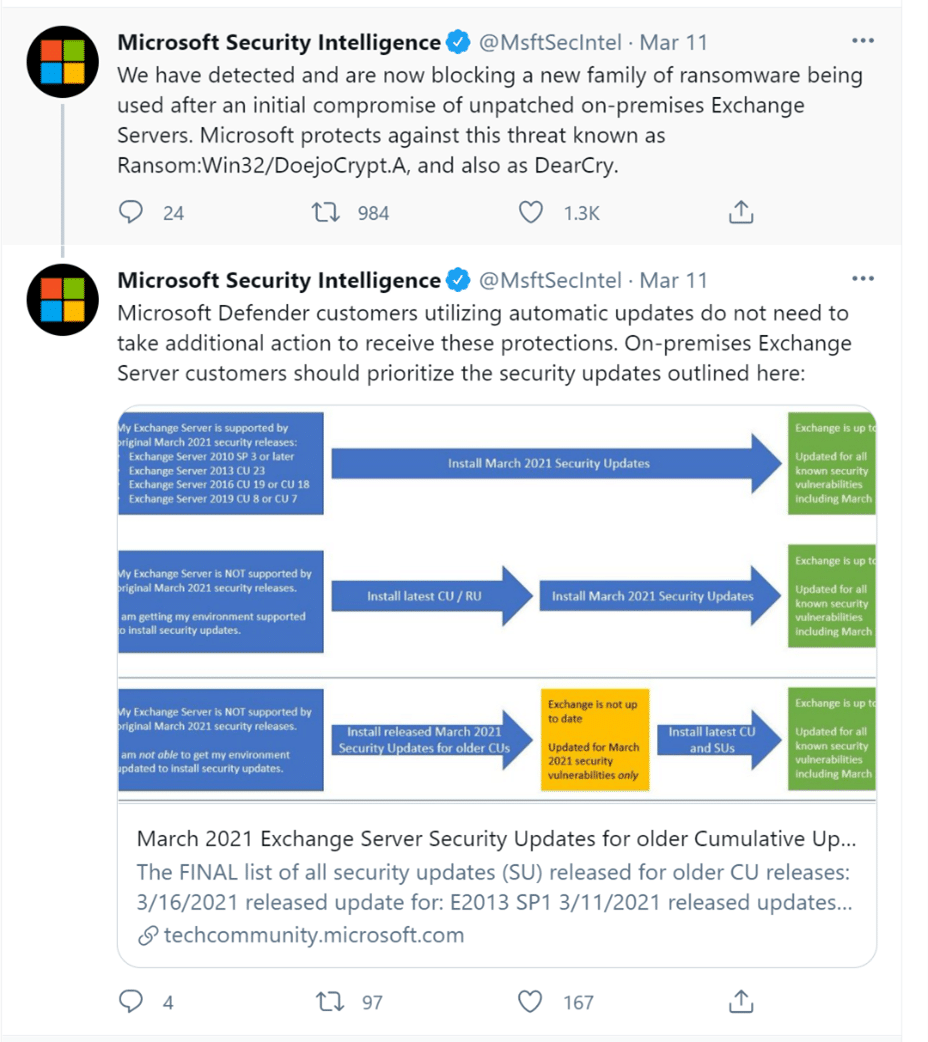
For those who are not administrating or fixing these things, Exchange is a widely adopted mail server technology. If you are utilizing Outlook right now, the chances are that you are connected to Exchange.
This is important. As of March 13th, Security experts at Palo Alto Networks estimated that at least 20,000 US-based Exchange servers remain unpatched and vulnerable to exploitation, and as many as 80,000 worldwide.
How can that be possible if Microsoft released a patch the same day? Aren’t these organizations taking a chance that they are not the next news headline?
You are right, but patching is complex. Most large organizations are not patching their Exchange server and stopping for the day. There is a vetting and testing process that needs to be completed for EACH application. You need to understand the impact of the security fix first. What will happen to your user experience? Will my users be able to send and receive emails and at the rate they are used to? I use Exchange as an example, but this applies to any applications that your organization may rely on for revenue.
Officials at the White House would agree. As attacks leveraging the vulnerabilities have escalated, the window for updating exposed servers is incredibly short — “measured in hours, not days,” a senior administration official told reporters.
To make matters worse – the pace of change in our IT environments is accelerating. In this last year alone, Microsoft updated Windows 10 more than 1,280 times. At the current trajectory of change, we could expect Microsoft to bring out 60,000 changes by 2030! Now is the time to start embracing this faster pace of change.
threatpost.com/microsoft-patch-tuesday-holidays/162041/
- 2019: 840 patches, many of which were “critical.”
- 2020: 1,250 patches, with a Dec-20 run-rate of 90+ releases/month
So, what can we do about the fact that, on average, it takes organizations 70 days (about 2 and a half months) to roll out patches? edgescan WITHOUT adding additional headcount. We need to automate every bit possible. We need to create a crucial point of visibility into the process. We need to have metrics that are easily distilled down. We also need a repeatable testing process.
Are you looking for a way to remediate vulnerabilities within your environment faster? We can assist with that. If you would like to schedule a demonstration of the combined products, please email us or request a trial license.
This blog was co-authored by Todd Kirkland, Chief Operating Officer at JetPatch.
PartnerPatching
