Image Change Control
Image Change Control
Automatically detect application failures and performance
disparities before and after updates, mitigating unexpected
issues from the start.
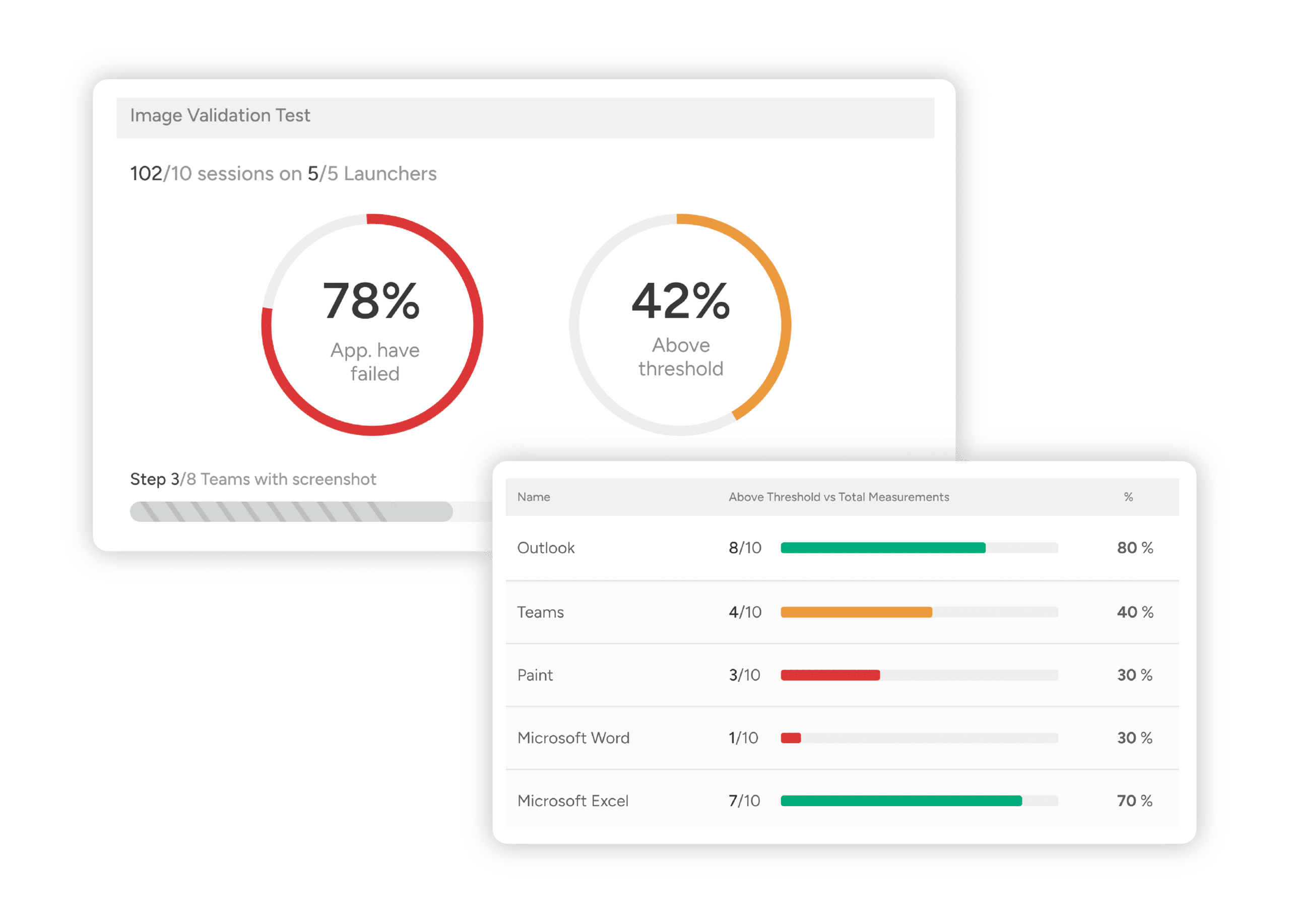
Planned and unplanned changes can trigger major service disruptions, especially with today’s high volume of software updates and patches. It’s time to ditch your manual efforts in favor of automation. Let our virtual users scale your efforts for maximum coverage and repeatable results—ensuring your most critical applications and EUC environments run consistently and perform reliably.
Reduction in time spent
validating changes
Reduction in time spent
resolving issues
Reduction in helpdesk tickets
Faster Change Cycles,
Less Risk
- Reduce the time needed to execute repetitive, manual tests and focus on more strategic initiatives.
- Eliminate the risk of human error, ensuring tests are performed precisely and consistently every time.
- Handle a vast array of tests simultaneously, providing coverage that’s impossible to achieve manually.
Catch Issues Before Rollouts
- Replicate user interactions to validate application functionality beyond simple login times.
- Identify and resolve compatibility issues for a smoother, interruption-free user experience.
- Ensure applications, drivers, and systems work cohesively across various configurations.
Maintain Consistent Experiences
- Leverage the same pre-production tests after deployment.
- Establish benchmarks to measure the impact of any change.
- Compare results over time to maintain similar experiences in production.
Explore Use Cases
Image Testing
Thoroughly test desktop images for functionality and performance before going live, significantly reducing downtime and increasing deployment confidence.
Learn MoreApplication Validation
Ensure applications perform as expected by simulating real-user activities to verify functionality, compatibility, and performance before deployment.
Learn MoreAgent Impact Analysis
Make informed decisions to maintain optimal performance when changing system tools and agents, such as endpoint security.
Learn More

