Security Impact Analysis
Security Impact Analysis
Make informed decisions to maintain optimal
performance when changing system tools and agents.
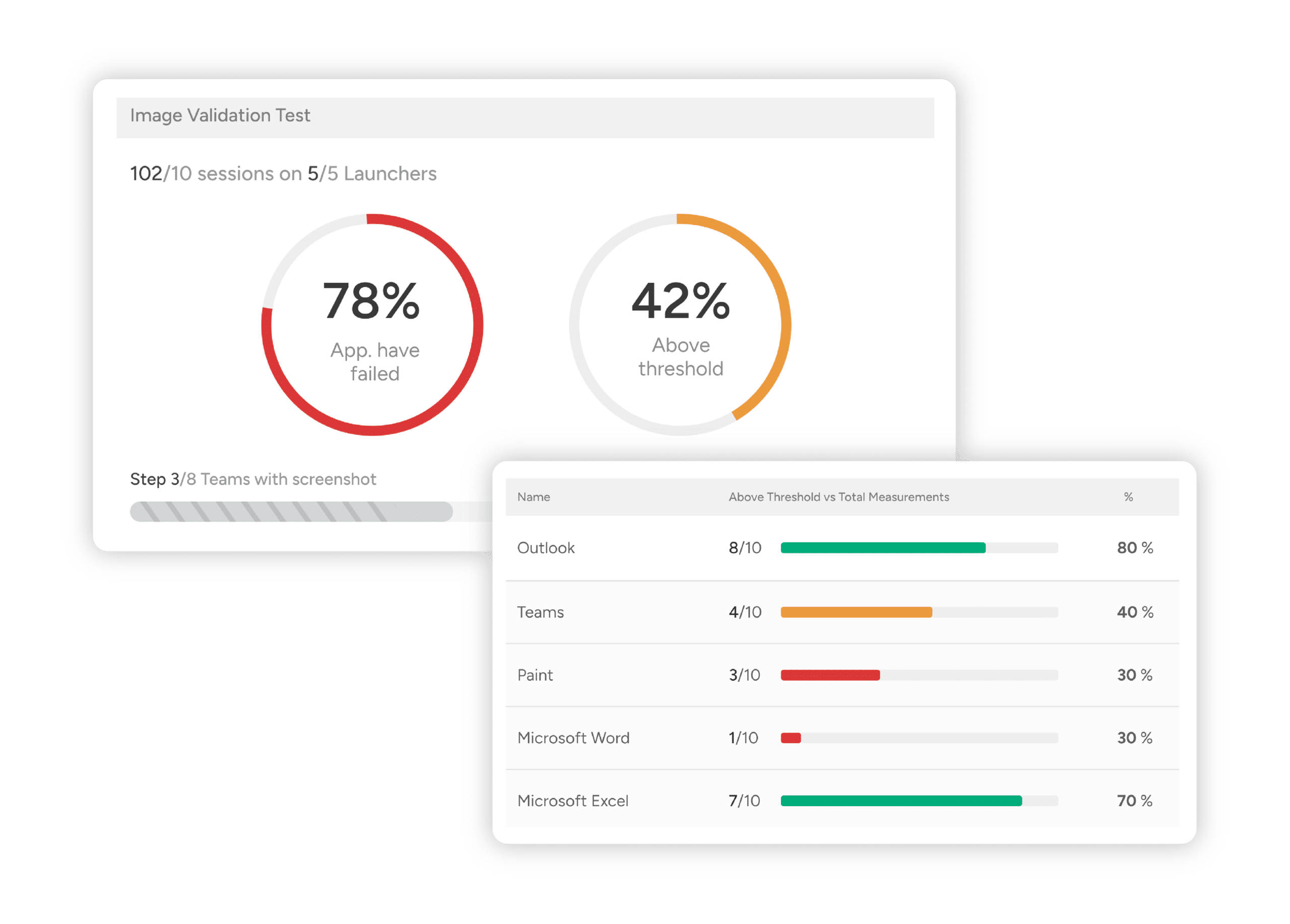
EUC teams frequently find themselves in a challenging position. They are often not in charge of selecting and configuring various agents, especially security-related ones; however, they are commonly blamed for any resultant poor performance. This situation leaves EUC teams without a quantifiable way to demonstrate the impact of these agents on performance, a critical factor in maintaining system efficiency and user satisfaction.
The Login Enterprise Platform provides comprehensive insights for benchmarking agent impact within a desktop image, enabling a deep understanding of how each agent affects system performance. Armed with real data and validation testing, Login Enterprise aids in making smarter decisions when introducing new tools and ensures critical policies remain functional and effective. This multifaceted approach not only enhances performance but also upholds higher levels of security.
Benchmark Agent Impact
- Gather detailed metrics and assess the performance impact of agents within a desktop image.
- Utilize real-time testing to track the impact of agents on system resources like CPU, memory, and disk usage.
- Leverage historical data to understand trends and patterns in agent performance over time.
Make Smarter Decisions
- Test and compare the compatibility and performance of new agents with your existing environments.
- Share results with security teams to guide purchasing decisions.
- Evaluate the impact before full-scale deployment to remediate and optimize configurations.
Validate Policies and Settings
- Create simple pass/fail list of tests to streamline post-change troubleshooting.
- Continuously validate any OS and security settings, ensuring they function as intended.
- Benefit from automated alerts that notify you of any issues, enabling quick response.
Explore Similar Use Cases
Image Testing
Thoroughly test your images for functionality and performance before going live, significantly reducing downtime, and providing IT with confidence in the deployment.
Learn MoreApplication Validation
Ensure that applications perform as expected under various scenarios by simulating real-user activities to verify functionality, compatibility, and performance.
Learn More

